About a month ago I was challenged by a customer to protect the key company personnel from Domain Administrators (Basically his IT department). This is a small company, less than 40 employees. At first I was confused as to why he wanted to do something like that, then I was frustrated at the amount of time it would take to implement a satisfactory solution for him, in addition to concerns about the cost.
There are real challenges to this type of request. First you can’t just remove all of the IT administrators from Domain Admins or Organization Management (Exchange) and expect them to be able to do their jobs. The IT team were developers as well and needed administrative rights to all sorts of systems in the organization. I could have taken on a lot of the responsibilities myself, but it would have been such a waste of money for the customer as they had perfectly capable people that could handle (and have been handling) all sorts of IT tasks over the years. Another challenge was these key employees use remote desktop over a VPN to access company network resources remotely. Keeping the remote access capability was a must.
Here is a summary of the solution I came up with:
To protect the user files:
1) Lock down his and the other key employees private files to their local workstation. On each of these workstations implement a local backup.
2) Remove Domain Admins from the Administrator group on these local workstations.
To alert on Active Directory and Exchange events:
3) Install Exchange 2010 SP3 (SP1 is the service pack that this important feature was first implemented) which logs administrative changes to Exchange (like taking ownership of a mailbox) to the Event Viewer.
4) Install a forwarding service on the domain controllers and Exchange server(s) to send all system events to a log server.
5) Install a log server with the ability to send email alerts upon seeing particular events (like Active Directory password changes and additions to groups).
6) Change Group Policy for the domain controllers to audit account management and policy changes.
Here is the procedure for accomplishing the most challenging part of this request (Logging Exchange and Active Directory events and having them send email alerts):
DOWNLOAD AND INSTALL KIWI SYSLOG SERVER:
1) Either build a new windows server for logging and alerting or use an existing server. Next install Kiwi Syslog (You need to purchase the commercial version 295.00 at the time of this post for the email alerting). It can be downloaded here: http://www.kiwisyslog.com/downloads.aspx. When installing just use the defaults.
DOWNLOAD AND INSTALL SNARE FOR WINDOWS ON THE DOMAIN CONTROLLERS:
Note: If it is a small company and both the domain controllers and the Exchange server are on the same server, then DO NOT install Snare for Windows, skip right to the next section “Installing Event Log to Syslog Service for Windows on Exchange”.
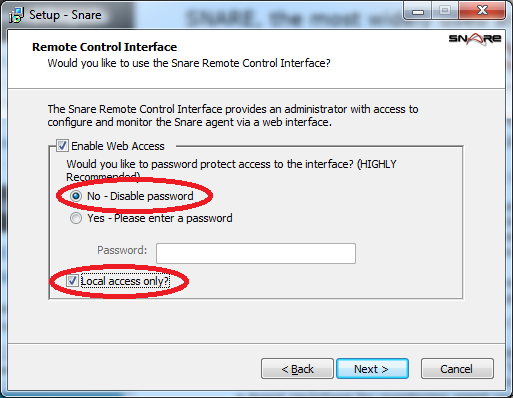
2) Install Snare for Windows on all domain controllers only (We will do something different with Exchange). Snare for Windows can be downloaded here: http://www.intersectalliance.com/projects/BackLogNT/. Use the defaults for the install, but when asked for “Remote Control Interface” I like to choose, “Enable Web Access”, “Disable the password” and check “Local access only?”. This allows only users that are logged into the actual server to make changes, you may want to change these settings to your personal preferences.
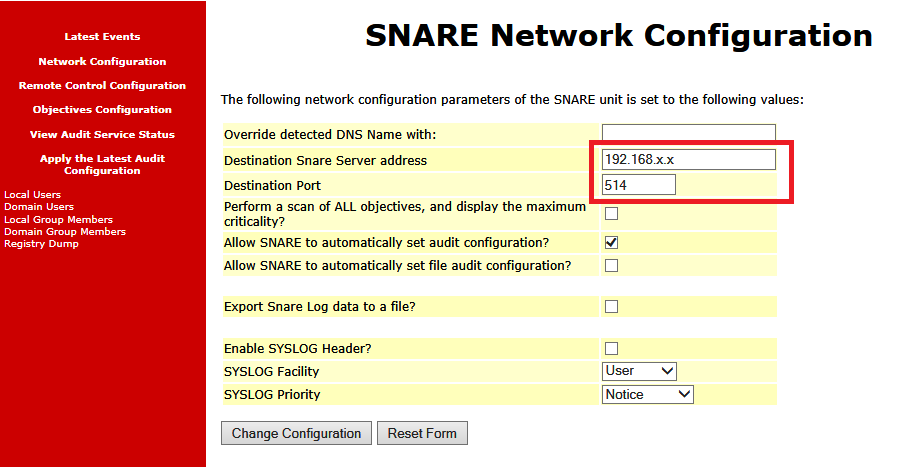
3) Once installed start “Snare for Windows” it’s icon is located in the Start Menu under “Intersect Alliance”. Click “Network Configuration” and enter in the IP address of the server running Kiwi Syslog Server and enter the “Destination Port” of 514.
4) Next click “Apply the Latest Audit Configuration” to the left and then click the “Reload Settings” button.
INSTALLING EVENT LOG TO SYSLOG SERVICE FOR WINDOWS ON EXCHANGE
Note: Exchange sends its events to the “MSExchange Management” log in event viewer. Snare doesn’t send these events (It only sends “Application”, “Security” and “System” events, which are fine for a domain controller, but not Exchange).
1) Download Evtsys (64bit version) to the Exchange server by clicking this link. http://code.google.com/p/eventlog-to-syslog/ then download the file to the left and extract the files to c:\windows\system32
2) Run the following command to install it as a service and start it.
evtsys -i -h <ip address of kiwi syslog server> net start evtsys
APPLYING AN AUDIT POLICY USING GROUP POLICY MANAGEMENT
1) From a domain controller run “Group Policy Management” from the Administrative Tools group.
2) Expand the tree to the left and right click on “Domain Controllers” and select, “Create and Link a GPO Here…”. Name the GPO “Domain Controller Audit Policy”.
3) Right click on “Domain Controller Audit Policy” and click “Edit”. Under “Computer Configuration” click to expand “Windows Settings”, then click to expand “Security Settings”, then click to highlight “Audit Policy”.
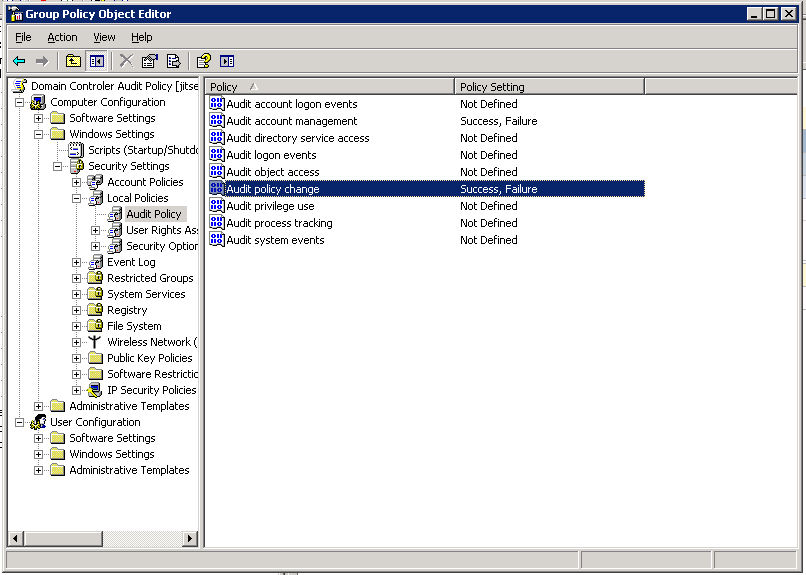
4) Double click “Audit account management”, check “Define these policy settings” then make sure both “Success” and “Failure” are checked and click OK.
5) Double click “Audit policy change”, check “Define these policy settings” then make sure both “Success” and “Failure” are checked and click OK. You should see a screen similar to the image below.
CONFIGURING KIWI SYSLOG TO EMAIL EVENTS
The customer wanted the following events emailed to him:
– When a user password is changed.
– When someone is made a Domain Admin.
– When someone is made an Exchange Admin (Member of the Organizational Management group).
– When someone takes control of someones mailbox.
1) Start the Kiwi Syslog Manager by clicking the Start Menu, then going to “All Programs”, then selecting “SolarWinds Kiwi Syslog Server”, then clicking, “Kiwi Syslog Server Console”.
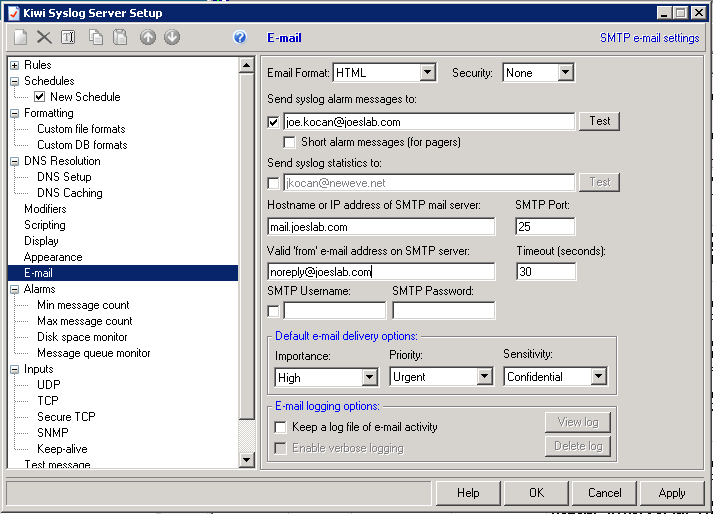
2) From the file menu, select setup and from the left, navigate down to “E-mail”. Populate the following fields with the correct information for your network:
– Place a check by “Send syslog alarm messages to” then enter the email address to the administrator of the syslog server.
– Enter the IP address or hostname of the mail server in the “Hostname or IP address of SMTP mail server” field.
– Enter an email address in the “Valid ‘from’ e-mail address on SMTP server”. I like to use “noreply@whateveryourdomainnameis.com” (If all alerts come in under “noreply” it is easy to search and delete alerts.
– If it is required fill in the “SMTP Username” and “SMTP Password” fields.
– Then click “OK”.
See the example in the picture below:
3) Create the first alert by right clicking on “Rules” to the left, then selecting “Add rule”, then give the rule a name. Let’s call the first rule “A New User Was Created” by typing that description as the name of the rule.
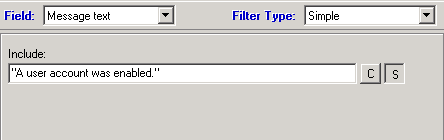
4) Next right click on the “Filters” selection under the new rule and select “Add filter”. At the top select “Message text” from the “Field” dropdown list. Then enter the following text in the “Include field” “A user account was enabled”. See image below.
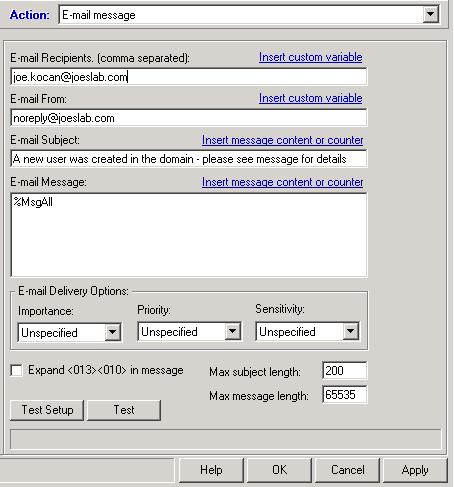
5) Next right click on “Actions” under the new rule and select “Add action”. From the “Action” pull dropdown list at the top choose “E-mail message”, then populate the following fields:
– E-mail recepients with the e-mail addresses of the people who need to be aware of the activity.
– E-mail from with the noreply or other address we used to setup the e-mail.
– E-mail subject, a description of the alert. In this case “A new user was created in the domain – please see message for details”.
– E-mail message, replace the default of “%MsgText” with “%MsgAll”, this will send the entire event rather then just part of it (I have found the entire message is useful in larger environments.
– Then click “OK”
See the example picture below:
6) Use the following table to create the rest of the alerting rules using the same steps above (3 through 5):
| Description | Message Text in include field | And field (for Complex filter) | Filter Type |
|---|---|---|---|
| User is created on a Windows 2008 DC | "A user account was enabled." | none | Simple |
| User is added to the Domain Admins group on Windows 2008 DC | "A member was added to a security-enabled global group." | Domain Admins | Complex |
| User is added to the Exchange Admins on Windows 2008 DC | "A member was added to a security-enabled universal group." | Organization Management | Complex |
| User password is changed on Windows 2008 DC | "An attempt was made to reset an account's password." | none | Simple |
| User password is changed on Windows 2003 DC | "User Account password set" | none | Simple |
| User is added to Domain Admins on Windows 2003 DC | "Security Enabled Global Group Member Added:" | Domain Admins | Complex |
| User is added to Exchange Admins on Windows 2003 DC | "Security Enabled Universal Group Member Added:" | Organization Management | Complex |
| Take full access rights over mailbox | "Add-MailboxPermission" | "AccessRights={FullAccess}" | Complex |
FINALLY – TEST
Test by performing the following actions and look for e-mail alerts:
1) Create a new test user with a mailbox.
2) Change the test users password from Active Directory Users and Computers.
3) Add that new user to the “Domain Admins” group.
4) Add that new user to the “Organization Management” group.
5) Add full access rights to the test user mailbox using the Exchange Management Console.
An e-mail alert should be received for each of the events.


Hey There. I found your weblog the use of msn. That is a very neatly written article. I’ll make sure to bookmark it and return to read more of your helpful info. Thank you for the post. I’ll certainly return.